Milestone-Proposal:Colossus
To see comments, or add a comment to this discussion, click here.
Docket #:2024-03
This proposal has been submitted for review.
To the proposer’s knowledge, is this achievement subject to litigation? No
Is the achievement you are proposing more than 25 years old? Yes
Is the achievement you are proposing within IEEE’s designated fields as defined by IEEE Bylaw I-104.11, namely: Engineering, Computer Sciences and Information Technology, Physical Sciences, Biological and Medical Sciences, Mathematics, Technical Communications, Education, Management, and Law and Policy. Yes
Did the achievement provide a meaningful benefit for humanity? Yes
Was it of at least regional importance? Yes
Has an IEEE Organizational Unit agreed to pay for the milestone plaque(s)? Yes
Has the IEEE Section(s) in which the plaque(s) will be located agreed to arrange the dedication ceremony? Yes
Has the IEEE Section in which the milestone is located agreed to take responsibility for the plaque after it is dedicated? Yes
Has the owner of the site agreed to have it designated as an IEEE Milestone? Yes
Year or range of years in which the achievement occurred:
1944-1945
Title of the proposed milestone:
The Colossus Computers, 1944-1945
Plaque citation summarizing the achievement and its significance; if personal name(s) are included, such name(s) must follow the achievement itself in the citation wording: Text absolutely limited by plaque dimensions to 70 words; 60 is preferable for aesthetic reasons.
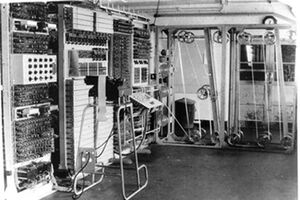
Six Colossus codebreaking computers operated in this building in 1944-1945. Designed by Thomas H. Flowers of the British Post Office, they enabled deciphering of encrypted radio messages transmitted between German commands across occupied Europe, North Africa, and the Soviet Union. The resulting military intelligence saved countless lives and helped shorten World War II. As the first successful large-scale application of digital electronics to computing, Colossus anticipated subsequent computer developments.
200-250 word abstract describing the significance of the technical achievement being proposed, the person(s) involved, historical context, humanitarian and social impact, as well as any possible controversies the advocate might need to review.
The Colossus codebreaking computers were developed to attack the World War II German Lorenz SZ50/52 teleprinter cipher used to encrypt radio traffic between Berlin and the major German commands across Europe, North Africa, and the Soviet Union.
The use of Colossus significantly improved the ability of Bletchley Park to break the Lorenz cipher compared to manual methods and electromechanical machines, and made a significant contribution to victory in Europe, due to the strategic nature of the intelligence gained.
Colossus was developed by a team led by Tommy Flowers from the British Post Office research station at Dollis Hill in London.
The first Colossus was delivered in January 1944, followed over the next 17 months by a further nine.
For its time, Colossus was an electronic tour-de-force. It used circuits for counting and Boolean algebra functions to perform statistical analysis of encrypted messages. Input was via a 5,000 character per second photoelectric paper tape reader and output to an online typewriter. Containing over 2,400 thermionic valves (vacuum tubes), Colossus was significantly larger than any other contemporary digital electronic device and ran continuously 24 hours a day, seven days a week. It was programmed using switch panels and jack leads to set up the desired computations. In many respects Colossus anticipated the modern electronic digital computer.
This proposal seeks recognition of Colossus as the first use of large-scale digital electronics in computing and for its contributions to the Allied victory in 1945.
IEEE technical societies and technical councils within whose fields of interest the Milestone proposal resides.
IEEE Computer Society, IEEE Communications Society
In what IEEE section(s) does it reside?
United Kingdom and Ireland
IEEE Organizational Unit(s) which have agreed to sponsor the Milestone:
IEEE Organizational Unit(s) paying for milestone plaque(s):
Unit: United Kingdom and Ireland
Senior Officer Name: Paul Cunningham (Chair)
IEEE Organizational Unit(s) arranging the dedication ceremony:
Unit: United Kingdom & Ireland
Senior Officer Name: Paul Cunningham (Chair)
IEEE section(s) monitoring the plaque(s):
IEEE Section: United Kingdom and Ireland
IEEE Section Chair name: Paul Cunningham (Chair)
Milestone proposer(s):
Proposer name: Dr Andrew Herbert OBE FREng
Proposer email: Proposer's email masked to public
Please note: your email address and contact information will be masked on the website for privacy reasons. Only IEEE History Center Staff will be able to view the email address.
Street address(es) and GPS coordinates in decimal form of the intended milestone plaque site(s):
Block-H, Bletchley Park, Milton Keynes MK3 6EB, United Kingdom
51.9984° N, 0.7437° W
Describe briefly the intended site(s) of the milestone plaque(s). The intended site(s) must have a direct connection with the achievement (e.g. where developed, invented, tested, demonstrated, installed, or operated, etc.). A museum where a device or example of the technology is displayed, or the university where the inventor studied, are not, in themselves, sufficient connection for a milestone plaque.
Please give the details of the mounting, i.e. on the outside of the building, in the ground floor entrance hall, on a plinth on the grounds, etc. If visitors to the plaque site will need to go through security, or make an appointment, please give the contact information visitors will need.
Site: Block-H, Bletchley Park, Bletchley, MK3 6DS, UK.
Block-H is one of many historical buildings on Bletchley Park dating from World War II. It was constructed specifically to house codebreaking machines, cryptographers, engineers and associated staff. Six Colossus machines were installed and operated in Block-H from 1944 to 1945.
In 2017 Block-H was listed in by Historic England as one of England’s “100 Irreplaceable Places” (https://historicengland.org.uk/campaigns/100-places/science-discovery/#Section4Text).
Block-H has been accorded Listed Grade 2 Status by the Historic Buildings and Monuments Commission for England, signifying that it is “of special interest, warranting every effort to preserve it.”
The building is owned by the Bletchley Park Trust but outside the perimeter of their Bletchley Park codebreaking museum.
Block-H is publicly accessible from the main entrance to Bletchley Park via a direct access road leading to The National Museum of Computing (http://www.tnmoc.org).
Are the original buildings extant?
Block-H is the only surviving of the two original buildings that housed the ten Colossus machines. The first four Colossus machines were installed in the adjacent Block-F which was demolished in recent years to create a car park. The subsequent six machines were in Block-H.
Details of the plaque mounting:
The plaque will be mounted on an external wall, adjacent to the main entrance of the UK National Museum of Computing which is the present day occupant of Block-H.
How is the site protected/secured, and in what ways is it accessible to the public?
Bletchley Park is a secured site with entrance via a controlled gatehouse. Visitors can enter via the main gate and drive/walk to Block-H without having to pay a fee. The Bletchley Park Trust web site gives opening times for the park. Generally it is open all year during daytime hours, except for 24th, 25th and 26th December.
Who is the present owner of the site(s)?
The Bletchley Park Trust. The UK National Museum of Computing occupies Block-H as a tenant of the Bletchley Park Trust.
What is the historical significance of the work (its technological, scientific, or social importance)? If personal names are included in citation, include detailed support at the end of this section preceded by "Justification for Inclusion of Name(s)". (see section 6 of Milestone Guidelines)
What was the significance of Colossus?
Colossus was the first successful large-scale application of digital electronics in computing and anticipated many aspects of the modern electronic digital computer.
What was Colossus?
Colossus was a codebreaking computer developed at the British Government Code and Cypher School (GC&CS) at Bletchley Park, in World War II. Colossus machines were used in the cryptanalysis of the German Lorenz SZ50/52 teleprinter cipher that secured radiotelegraphy messages passing between the German High Command and the German commands in occupied Europe, North Africa, and the Soviet Union. The British code name for messages transmitted using this cipher was “Tunny.”[1]
The Lorenz machine had twelve rotating wheels and used a Vernam ciphering technique on message characters encoded in the standard 5-bit ITA2 telegraph alphabet. It did this by combining the plaintext characters with a stream of key characters using the XOR Boolean function to produce the ciphertext. The key stream was generated by three sets of wheels named by the Bletchley codebreakers χ (“chi”), ψ (“psi”) and μ (“mu”) respectively. Each wheel had a series of cams (or pins) around their circumference. These cams could be set in a raised (active) or lowered (inactive) position. In the raised position they generated a ‘1’ which, when XOR-ed with a bit, reversed its value; in the lowered position they generated a ‘0’ which, when XOR-ed, left the bit unchanged. The number of cams on each wheel equalled the number of impulses needed to cause them to complete a full rotation. These numbers were all co-prime, giving the longest possible sequence before the pattern repeated. The number of possible settings of the machine was the product of the number of positions of the wheels. For the set of χ wheels it was 41 × 31 × 29 × 26 × 23 = 22,041,682 and for the ψ wheels it was 43 × 47 × 51 × 53 × 59 = 322,303,017. Thus, the number of different configurations that all twelve wheels could be set was 1.603×1019 i.e. 16 billion, billion, presenting a formidable cryptographic challenge.[1]
From 1943 onwards the British had developed manual methods to break intercepted Tunny messages, but these were slow, devaluing the timeliness and intelligence value of the eventual decrypt. Building on the earlier experience of using electromechanical machines to attack the simpler Enigma machine ciphers, Bletchley Park had created a semi-electronic / semi-electromechanical machine called “Heath Robinson” to automate some of the analysis, but the Heath Robinsons were unreliable and relatively slow. Using digital electronic circuits, Colossus was a major evolutionary step forward with a significant increase in both reliability and speed.[1]
Colossus used digital circuit elements built from thermionic valves (vacuum tubes) to perform Boolean and counting operations on intercepted messages. Colossus anticipated the subsequent development of modern computers, in that it was electronic, digital, and programmable. Input consisted of encrypted message text punched on paper tape. It was programmed by manually configuring switches and patching cables between telephone jack sockets. By these means it was possible to set up Boolean operations to match patterns on the input tape and to count occurrences of those patterns. Thresholds could be set that, when reached, would produce output on an online typewriter.[1]
Colossus was conceived by Thomas (Tommy) Harold Flowers, a research engineer working at the British General Post Office (GPO) research station at Dollis Hill in North London where he oversaw the 50 strong telephony switching group. Flowers had been involved in the development of the electronic aspects of Heath Robinson and was aware of its limitations. He formed the view that it would be better to have a fully electronic machine. The overall concept of Colossus was Flowers’ work,[1] with the assistance of his Dollis Hill colleagues William Chandler and Sidney Broadhurst, and then later Allen Coombs, and also with input from Eric Speight and Arnold Lynch.[2]
Work on Colossus began early in 1943. It took Flowers and his team at the Post Office’s Dollis Hill research station in North London 10 months to complete the first machine, working day and night, pushing themselves until (as Flowers said) their “eyes dropped out.”[3] The prototype Colossus first operated successfully in December 1943 at the Post Office’s Dollis Hill research station and was subsequently transferred to Bletchley Park in January 1944.[4]
An improved Colossus that included shift registers to quintuple the processing speed, first ran satisfactorily on 1 June 1944, just in time for the Normandy landings on D-Day (6th June 1944) and consequent battles until the end of World War II. In total, ten Colossus machines were in use by the end of the war in 1945, all to the improved design, and an eleventh was being commissioned.[5]
Bletchley Park’s use of these machines allowed the Allies to obtain a large quantity of strategic high-level military intelligence more quickly and in greater volume than had been possible with the manual methods and electromechanical machines they had relied on prior to the advent of Colossus. As stated in the General Report: “[the arrival of Colossus] immediately sent up the output [of decrypted messages] to more than twice its previous level.”[1]
A significant example of the intelligence obtained from breaking Tunny relates to D-Day, 6th June 1944, when the Allies in World War II launched their seaborne assault on Nazi Germany’s “Fortress Europe” towards Normandy in France. Their biggest fear was that their forces would fail to overcome German resistance at the beaches. Reassuringly, in the days immediately before D-Day, they received intelligence that Hitler, the German leader, had fallen for the Allies’ deception efforts: he believed the main attack would come later, to the North at the Pas de Calais, and held back his reserves from counter-attacking the landings. As is told by history, the invasion was successful, and by May 1945 the war in Europe was over and Nazi Germany defeated. This vital intelligence came from the decryption of Tunny messages transmitted by radio from the German HQ in Berlin.[6] We do not know precise details of how these messages were decrypted but we do know Colossus was available in time to help.[7]
Operating Colossus
Located in Block-F and Block-H at Bletchley Park, the Colossus machines were operated by a section known as the “Newmanry,” after its head, the mathematician Max Newman. Newman’s section’s job was to develop and employ machine methods for cryptanalysis of the Lorenz cipher. It was staffed by cryptanalysts, operators from the Women’s Royal Naval Service (WRNS) – known as “Wrens” – and Post Office engineers who were permanently on hand for maintenance and repair. By the end of the war the staff was comprised 272 Wrens and 27 men.[1]
Lorenz messages were intercepted at radio listening post outstations. Here the radio signals were recorded and manually translated into characters from the International Telegraph Alphabet number 2 (ITA 2) and punched to paper tapes which were then sent to Bletchley Park for decryption. The challenge for the codebreakers was to determine the settings of the Lorenz machine used to send the encrypted message. The machine settings comprised the start positions and cam settings of the twelve interlinked wheels forming the encrypting element of the machine. The codebreakers had developed methods for analysing Tunny messages to determine the machine settings. Once the machine settings were known, the message could be decrypted into the original German plaintext and passed to further sections at Bletchley Park for cataloguing and interpretation. The intelligence so gained would then, as appropriate, be distributed to the Allied leadership and command.[1]
The first job in operating Colossus for a new message was to prepare a paper tape loop containing the message to be analysed. This was performed by the Wrens who stuck the two ends of the tape together using glue, ensuring that there was a 150-character length of blank tape between the end and the start of the message. Using a special hand punch, they inserted a start hole between the third and fourth channels 21⁄2 sprocket holes from the end of the blank section, and a stop hole between the fourth and fifth channels 11⁄2 sprocket holes from the end of the characters of the message. These were read by specially positioned photocells and indicated when the message was about to start and when it ended.[5]
The operator would then thread the paper tape through a gate and around the pulleys of a transport mechanism (known as the bedstead on account of its appearance) and adjust the tape tension. The bedstead was arranged such that one tape could be loaded whilst another previous one was being run. A switch controlled whether Colossus read the near or the far tape in the bedstead.[5]
After performing various resetting and zeroing tasks, the Wren operators would, under instruction from a cryptanalyst, set up a bank of panel switches and jack plug connections for the desired pattern searches. In addition, a series of decade switches were set to indicate thresholds at which pattern match counts were to be reported. The Wrens would then start the bedstead tape motor and illuminate the photoelectric tape reader lamp. When the tape was up to speed (5,000 characters per second), the Wrens would operate the master start switch. The machine would then process the tape calculating totals according to the programmed settings and the resulting counts would be output to a modified IBM electric typewriter. These would be given to the cryptanalyst who would use the computed results to deduce the Lorenz machine settings for the enciphered message and eventually have it translated to German plaintext.[5]
Programming Colossus
Colossus processed each of the individual channels of the paper tape input in parallel. Different processing could be applied to each channel. The programs for each channel were set on panel switches (the selection switches) and on jack plugs inserted in panels of jack sockets. For each channel Colossus could evaluate a Boolean function and count and display the number of times it yielded the specified value of false (0) or true (1) for each pass of the message tape.[1][5]
Input to the Boolean and counting functions came from two sources: shift registers loaded by reading the paper tape channels as the message tape passed through the photoelectric reader, and from a set of thyratron rings that emulated the rotors of the Lorenz machine.[5]
The message characters on the paper tape were called Z and the keystream characters from the Lorenz emulator were referred to by the Greek letters associated with the χ (chi) and ψ (psi) wheels. On the selection panel, switches specified either Z or ΔZ, either χ or Δχ and either ψ or Δψ for the data to be passed to the jack field and the switch panel. (The symbol Δ denoting the difference between successive bits in a channel.) Additionally, the signals from the wheel simulators could be specified as stepping on with each new pass of the message tape or not.[1][5]
The switch panel had one group of switches (on the left-hand side of Colossus) to specify the patterns to count. Switches on the right-hand side selected the counter to which the result was fed. The plugboard allowed Boolean conditions to be imposed on the input paper tape. Overall, the switches and the plugboard allowed for about five billion different combinations of the selected variables.[1][5]
As an example: a set of runs for a message tape might initially involve two χ wheels. Such a two-wheel run was called a long run, taking on average eight minutes, unless the parallelism was utilised to cut the time by a factor of five. The subsequent runs might only involve setting one χ wheel, giving a short run taking about two minutes. Initially, after the initial long run, the choice of the next algorithm to be tried was specified by the cryptanalyst. Experience showed, however, that pre-planned decision trees for this iterative process could be produced for use by the Wren operators in a proportion of cases.[1][5]
Colossus and the Modern Computer
To many audiences in the 21st century, the term “computer” might tend to conjure up nothing but our modern, all-purpose digital machines, each of them an electronic, von Neumann-type, binary computer executing symbolically encoded instructions stored in an internal, addressable, read-write memory. But not all modern computers are like that of course (there are special-purpose computers, analogue computers, massively parallel computers, quantum computers, dataflow architecture computers, DNA computers, etc), and nor were many of the pioneering computers that ushered in the modern age. The famous ENIAC (Electronic Numerical Integrator and Computer)[8] (IEEE Milestone: https://ethw.org/Milestones:Electronic_Numerical_Integrator_and_Computer,_1946) was a decimal computer, not binary, and for several years was programmed in much the same way as Colossus, using switches, cables and plugs. Not until 1948 were ENIAC’s instructions executed from memory, and even then, the program memory was read-only, not read-write. The Harvard Mark I Computer (1943) (IEEE Milestone https://ethw.org/Milestones:Harvard_Mark_I_Computer,_1944_-_1959#Title) was electromechanical, not electronic, and it drew its instructions from punched tape, not from an internal memory. Konrad Zuse’s Z3 (1941), described by Zuse as the “first program-controlled computer which worked as a complete entity”[9] was also relay-based, and, like the Harvard Mark I, was controlled by punched tape. Postwar electromechanical tape-controlled computers, such as the Harwell Dekatron Computer (1951)[10] and Zuse’s Z4 (1945), Z5 (1953) and Z11 (1955), enjoyed a surprisingly long lifespan, with some models still in use in the early 1960s. These electromechanical computers were, if not completely all-purpose, certainly able to carry out a wide range of different tasks, while the early electronic computers on the other hand were far from all-purpose. The electronic Atanasoff–Berry Computer (1939-42), (IEEE Milestone https://ethw.org/Milestones:Atanasoff-Berry_Computer,_1939), which predated both Colossus (1943-45) and ENIAC (1945), was designed as a special-purpose solver of systems of linear algebraic equations. Colossus itself was by design restricted to the kinds of calculations necessary for cracking Tunny messages.
In short, computers, as understood by historians of computing, are a diverse family of machines. During the prewar years, the word “computer” began to transcend its original role, in which it designated human calculating clerks, and it came to be the term for the new computing machines then being built to carry out, at high speed, the calculating work done hitherto (if done at all) by human computers.[11][12]
Two early writers to use “computer” in its new sense were George Stibitz and Alan Turing. Stibitz, a leading proponent of the electromechanical paradigm, wrote in 1940 of building “a complex computer … employing relays,”[13] and ten years later Turing explained, in the opening paragraph of his programming manual for the Manchester Mark 1 computer, that “Electronic computers are intended to carry out any definite rule of thumb process which could have been done by a human operator working in a disciplined but unintelligent manner.” [14]
Like the Atanasoff–Berry Computer, Colossus harnessed the speed of vacuum tubes to carry out mathematical tasks that would consume unrealistic amounts of time if carried out by human computers. General agreement exists among scholars that Colossus is appropriately termed a computer[2][15][16][17][18] (though, as is often the case in the academic world, agreement is not completely universal; see for example Haigh 2018[19] and the response in Price 2021.)[20]
The wartime mathematicians and engineers who were responsible for Colossus and its extraordinary successes were of the same view. Mathematician Bill Tutte — creator of the wheel-setting and wheel-breaking algorithms run by Colossus — said of Bletchley Park, in a 1999 lecture: “there an electronic computer was invented more than half a century ago.”[21] Jack Good, another of the Bletchley Park mathematicians, said “Colossus could be regarded as the first large-scale electronic computer, albeit for a specialised purpose, but leaning towards being general-purpose.”[22] With Donald Michie, Good was the first to demonstrate (in 1944) that Colossus had sufficient flexibility to carry out, not only the originally specified task of wheel-setting, but also the very different job of wheel-breaking. Moreover, he reported that, after the war, he experimented with “verifying how flexible was the Boolean plugging of Colossus in principle,” concluding that Colossus was “more general-purpose than its designer intended.”[22] Flowers himself said that Colossus, with its elaborate facilities for logical operations, was “much more of a computer than ENIAC.”[23][24] Flowers’ engineer Don Horwood, who helped build the Colossus machines, and was the author of “A Technical Description of COLOSSUS I” (declassified in 2003), emphasised that Colossus was “the first large-scale electronic computer.”[25]
The impact of Colossus on Subsequent Developments
Colossus and the reasons for its construction were highly secret and remained so for 30 years after World War II. Consequently, it was not included in accounts of the history of computing hardware for many years, and Flowers and his associates were deprived of the recognition they were due.[7] All but two of the Colossus machines were dismantled after the war and parts returned to the Post Office. Some parts, sanitised as to their original purpose, were taken to Max Newman’s Royal Society Computing Machine Laboratory at Manchester University where the world’s first electronic digital stored-program computer to use a read-write memory was developed and demonstrated in 1948 (IEEE Milestone [https://ieeemilestones.ethw.org/Milestone-Proposal:The_Manchester_University_%27Baby%27_computer;_Small-Scale_Experimental_Machine_(SSEM)]). The two surviving Colossus machines were moved to GCHQ's new headquarters at Eastcote in April 1946, and then to Cheltenham between 1952 and 1954. One of them known as Colossus Blue, was dismantled in 1959; the other, Colossus Red, in the 1960s.
Tommy Flowers was ordered to destroy all his Colossus documents. He duly burnt them in a furnace and later said of the order: “That was a terrible mistake. I was instructed to destroy all the records, which I did. I took all the drawings and the plans and all the information about Colossus on paper and put it in the boiler fire. And saw it burn.”[26] Fortunately, his colleague Coombs's documents survived.
The retained machines were adapted for other purposes, with varying degrees of success; in their later years they were used for training. Jack Good, one of the Bletchley cryptographers related how he was the first to use Colossus after the war, persuading the US National Security Agency that it could be used to perform a function for which they were planning to build a special-purpose machine. Colossus was also used to perform character counts on one-time pad tapes to test for non-randomness.[22]
In 2024, celebrating the 80th anniversary of the arrival of the first Colossus at Bletchley Park GCHQ released three photographs showing one of the surviving machines in a modified form together with some blueprints of Colossus’s inner workings.
A small number of the people who were associated with Colossus — and therefore knew that large-scale, reliable, high-speed electronic digital computing devices were feasible — went on to significant roles in early computer work in the UK. However, with Colossus being so secret, they could not reveal the source of their knowledge of electronic digital computing devices. Thus, Colossus had limited direct influence on the development of later computers. Herman Goldstine, an early computing pioneer, from the USA, who was unaware of Colossus and its legacy to the projects of people such as Alan Turing (ACE) and Max Newman (early Manchester computers), questioned why “Britain had such vitality that it could immediately after the war embark on so many well-conceived and well-executed projects in the computer field.” In response, Professor Brian Randell, of Newcastle University, UK, who unearthed information about Colossus in the 1970s, wrote: “It is my opinion that the Colossus project was an important source of this vitality, one that has been largely unappreciated, as has the significance of its places in the chronology of the invention of the digital computer.”[2]
Colossus Revealed
The first public information about the Colossus machines only appeared in 1972, arising from the research into the origins of digital computers by Brian Randell. He published an article entitled “On Alan Turing and the Origins of Digital Computers”[27] which pulled together fragments of anecdotal information from multiple sources to first describe Colossus.
As he describes in the paper, he approached the British Government, through the Prime Minister of the time, to seek the official release of information about Colossus. His request was rejected on the grounds of national security and even denial that there been British World War II developments in electronic computing.
The secrecy about Bletchley Park codebreaking was first exposed when Group Captain Winterbotham published his book “The Ultra Secret in 1974.” In October 1975, the first acknowledgement of the existence of Colossus by the UK Government came in a series of captioned photographs of a Colossus released by the UK Public Record Office.
Randell was allowed to interview the Colossus designers about their work on the wartime development of the Colossus at the Post Office Research station, though not its detailed design or use, and to prepare a paper on his findings, incorporating these photographs. A version of his paper was cleared for presentation at the conference on the history of computing held at the Los Alamos Scientific Laboratory, New Mexico, USA in June 1976.[28] The interest in his paper resulted in a special evening meeting when Randell, accompanied by Coombs from the original Colossus team, answered further questions. Coombs told the audience, “No member of our team could ever forget the fellowship, the sense of purpose and, above all, the breathless excitement of those days.” The following year (1977) Randell published an article, “The First Electronic Computer,” in the February edition of the UK popular science magazine “New Scientist,” sharing the story of Colossus with the wider public and 1980 he published an extended and updated version of his technical report as a book chapter.[2]
Since then, there has been considerable ongoing research into Colossus, the team that designed and built it, and how it was applied to breaking Tunny messages.
In 1983 a special edition of the IEEE Annals of the History of Computing journal, was dedicated to Colossus and contained a series of papers written by the pioneers who designed and built the machines revealing more details of the machines, their construction and operation.[5][29][30]
Eventually, in October 2000, GCHQ, the post war successor to GC&CS, deposited in the UK Public Records office a 500-page typescript technical report on the Tunny cipher and its cryptanalysis.[1] This report, hereafter referred to as the “General Report,” written by Bletchley staff at the end of the war laid out, for the first time in public, the whole incredible story of the Lorenz cipher and Colossus. It includes an eulogy to Colossus by the cryptographers who worked with it: “It is regretted that it is not possible to give an adequate idea of the fascination of a Colossus at work; its sheer bulk and apparent complexity; the fantastic speed of thin paper tape round the glittering pulleys; the childish pleasure of not-not, span, print main header and other gadgets; the wizardry of purely mechanical decoding letter by letter (one novice thought she was being hoaxed); the uncanny action of the typewriter in printing the correct scores without and beyond human aid; the stepping of the display; periods of eager expectation culminating in the sudden appearance of the longed-for score; and the strange rhythms characterising every type of run: the stately break-in, the erratic short run, the regularity of wheel-breaking, the stolid rectangle interrupted by the wild leaps of the carriage-return, the frantic chatter of a motor run, even the ludicrous frenzy of hosts of bogus scores.”
The General Report refers to a companion document giving a technical description of Colossus, but this is apparently lost. In 1973, GCHQ commissioned a replacement document entitled “A Technical Description of COLOSSUS I.”[31] This was written by D. C. Horwood, who had been a member of the Post Office team that built the first Colossus. This account was declassified in August 2003 and a copy deposited in the UK National Archives. The story of how it came to be written is told in the first paragraph: “This paper has been prepared to honour an undertaking given by GCHQ to prepare, and place in archives, a description of the early electronic computer-like equipment known as Colossus I. The decision to prepare this record followed representations, made by Professor B Randall [sic] of Newcastle University to the Prime Minister in January 1972, which sought the release of information on the machine so that it might be accorded an appropriate place in the history of the development of the modern electronic computer. After careful consideration it was decided that the information requested by Professor Randall [sic] could not be released at that time, but that a description of the machine should be prepared so that it would be available if it were to be decided, at some future date, that the information could be released.” There is also a description of what documentation was available inside GCHQ in 1973: “The decision to prepare the technical description having been taken, the next steps were to locate and assemble the available documents and diagrams and to produce a coherent record. This posed several problems. The design of the original machine was largely the work of Mr T H Flowers, at the time the senior Engineer in charge of what, in 1943, was known as the Signalling Group at the Post Office Research Station at Dollis Hill. Flowers, however, had retired and was no longer in any way associated with GCHQ. For security reasons all the official documents relating to the work at Dollis Hill had been handed over to GCHQ at the end of the War and unfortunately none of those relating to the original Colossus had been preserved.”
In 2006, Oxford University Press published Colossus: The Secrets of Bletchley Park's Codebreaking Computers containing extracts from the “General Report on Tunny”, together with seventeen first-hand accounts of Colossus and the Tunny-breaking process, as well as extensive analysis and commentary by historians.[16]
In 2015, Wiley-IEEE Press published Breaking Teleprinter Ciphers at Bletchley Park: An edition of I.J. Good, D. Michie, G. Timms – General Report on Tunny with Emphasis on Statistical Methods (1945).[32] This is an annotated version of the original General Report with commentary that clarifies the often difficult language of the original and fits it into a variety of contexts arising out of several separate but intersecting story lines, some only implicit in the original, including an exploration of the likely roots of the ideas entering into the Tunny cryptanalysis, examples of original worksheets, and printouts of the Tunny-breaking process in action along with additional commentary, biographies, glossaries, essays, and bibliographies.
While official documentation of the Colossus design from 1944-1945 remains lost, working from information in the General Report, descriptions given by Flowers and his colleagues in papers published in the IEEE Annals of History of Computing in 1983, the Oxford University Press collection in 2006,[16] and anecdotal evidence gathered from those who worked at Bletchley and Dollis Hill there is now a fairly complete understanding of the physical and electronic aspects of the machine, written up by several authors including Haigh[19] and Wells.[33]
A functioning reconstruction of a Colossus[17] was completed in 2008 by Tony Sale and a team of volunteers at the UK National Museum of Computing at Bletchley Park where it can be visited and is demonstrated throughout the day when the museum is open. The reconstruction sits exactly on the footprint occupied by the original ninth Colossus machine.
Moviemakers have enabled the Colossus story to reach a large audience internationally. Flowers and Colossus first gained widespread public recognition thanks to the BBC TV documentary “Code-Breakers: Bletchley Park’s Lost Heroes” (see https://www.imdb.com/title/tt2491866/). Directed by Julian Carey, and based on Jack Copeland’s book about Colossus,[16] the documentary was pick of the day in most UK national newspapers after airing to an initial audience of over 5 million, in October 2011. It went on to win two BAFTAs (British Academy of Film and Television Arts awards) in 2012, and in 2013 was named one of the year’s three best historical documentaries, at the Media Impact Awards in New York City. Since then, Code-Breakers has made regular appearances on the History Channel, PBS America and other international TV outlets. In 2013, the ARTE TV documentary “The Man Who Cracked the Nazi Code” was filmed in Block-H and elsewhere at Bletchley Park, premiering in Paris in 2014 and going on to win the audience’s Best Documentary prize at the 2015 FIGRA European film festival (see https://www.imdb.com/title/tt4515578/). Directed by Denis van Waerebeke and based on another of Jack Copeland’s books, The Man Who Cracked the Nazi Code has been translated into many languages and has been shown widely on TV networks around the world, including ARTE and the History Channel.
Alongside these major documentaries, there have been many YouTube videos made about Colossus. These are listed in the bibliography at the end of this proposal.
In 2015, the UK’s Royal Mail issued a commemorative postage stamp celebrating Colossus. The stamp displays an artist’s impression of 5-bit teleprinter tape and the legend “COLOSSUS world’s first electronic digital computer.”
Justification for Inclusion of Names
The citation names Tommy Flowers as the designer of Colossus. This is undisputed and supported by multiple sources. The General Report explicitly states in Section 15C(b) Colossus: “Colossus was entirely the idea of Mr Flowers of Dollis Hill.”[1] A 1943 letter from Newman to Travis (head of GC&CS) outlines Flowers proposal to build “an entirely different machine” [which] “would involve 5000 or so valves.”[34]
Flowers himself gives an account of his work in an article in the IEEE Annals of Computing History[5] and in two chapters of the 2006 Oxford University Press collection.[7][35]
His achievement is celebrated by an English Heritage Blue Plaque at the site of the former Dollis Hill Post Office research station, stating Flowers “designed and built the pioneering Colossus computer.”
What obstacles (technical, political, geographic) needed to be overcome?
Obstacles to Colossus
Colossus was the result of overcoming two technical obstacles: the first being the development of computational methods for decoding Lorenz messages and the second being the first ever construction of a large-scale electronic system to perform computations quickly and reliably. In terms of political obstacles there was scepticism from several at Bletchley Park that such a machine could be made to work, since it would be several orders of magnitude larger and more complex than contemporary uses of electronics in radio and radar systems. It is fortunate that Flowers had the prior experience from his work on automated telephone switching to be confident in his design for Colossus, and the tacit support of the Dollis Hill management that enabled him to build the prototype Colossus which so stunned the Bletchley codebreakers.
Breaking Tunny
In 1940 GC&CS became aware that the Germans were using teleprinter like stream cipher machines interconnected through a radio transmission system to carry messages encoded in the 5-bit International Telegraphy Alphabet No. 2 (ITA2). The British learned that the Germans called the system Sägefisch (Sawfish) and this led GC&CS to call the German teleprinter traffic “Fish,” and the unknown machine as “Tunny” (i.e. tuna fish) and its messages as “Tunny traffic.” [1]
In fact, the Germans had developed several online Geheimschreiber (secret writer) stream cipher machines. The principal of these and the one used for the Tunny traffic was the Lorenz SZ50/52 (SZ for Schlüssel-Zusatz, meaning “cipher attachment”).[1]
As described earlier, the Lorenz machine was a mechanical device implementing a Vernam type of cipher. With a sufficiently random keystream, a Vernam cipher removes the natural language property of a plaintext message of having an uneven frequency distribution of the different characters, to produce a uniform distribution in the ciphertext. The Lorenz machine did this well: it had twelve rotating wheels which were divided into two sets of 5 named χ and ψ respectively and a pair of “motor” wheels named μ. Each wheel had a series of cams (or pins) around their circumference. These cams could be set in a raised (active) or lowered (inactive) position. In the raised position they generated a ‘1’ which when XOR-ed with a bit reversed its value; in the lowered position they generated a ‘0’ which, when XOR-ed, left the bit unchanged. The number of cams on each wheel equalled the number of impulses needed to cause them to complete a full rotation.
The set of five χ wheels all moved on one position after each character had been enciphered. The five ψ wheels, however, advanced intermittently. Their movement was controlled by the two μ wheels acting in series. The SZ40 μ61 motor wheel stepped every time but the μ37 motor wheel stepped only if the first motor wheel was a '1'. The ψ wheels then stepped only if the second motor wheel was a ‘1’.
The first obstacle for the Bletchley codebreakers to overcome was to discover the logical structure of the Lorenz machine itself, which they had never seen. Once the structure of the machine was known, the second obstacle to overcome was that of the “wheel patterns”, i.e., the positions of the cams around the wheels, which were different for each of the Tunny communication links. From the summer of 1944 these were changed every 24 hours, so the search for the wheel patterns became a daily task.
In August 1941, a blunder by German operators led to the transmission of two slightly different versions of the same message with identical Lorenz machine settings.[36] These were intercepted and worked on at Bletchley Park. First, John Tiltman of the Bletchley Research Section derived, by hand, a keystream of almost 4000 characters. Then Bill Tutte, a newly arrived member of the Research Section, subsequently joined by colleagues, successfully used this keystream to attempt to work out the logical structure of the Lorenz machine in terms of the number of wheels, the number of cams in each wheel and the stepping mechanism. From this full understanding of the logical structure of the Lorenz machine, the Bletchley cryptographers worked out that, by examining the frequency distribution of the character-to-character changes in the cipher text instead of the individual characters, there was a departure from uniformity which provided a way into the system. This became known as “Tutte’s Statistical Method.”[1][37]
To decrypt the transmitted Tunny messages, two tasks had to be performed. The first was “wheel breaking,” which was the discovery of the cam patterns for each of the wheels. Alan Turing invented a pen and paper method of wheel-breaking that became known as “Turingery.”[1]
The second task was “wheel setting,” which involved working out the start positions of the wheels for a particular message and could only be attempted once the cam patterns were known. Each transmission, which often contained more than one message, was enciphered with a different start position for the wheels. Likely χ-wheel settings could be checked by examining the frequency distribution of the characters in the processed cipher text, resulting in a “de-χ” .[1]
The de-χ would then be passed to a group led by major Ralph Tester, known as the Testery, where the starting positions of the ψ wheels where determined by hand methods.[38] Once ψ and χ settings were known a further machine, confusingly also known as “Tunny,” would be set up to read in the cipher text and emit plaintext for passing on to the intelligence analysis sections at Bletchley.[1] (The Tunny machine was an electromechanical device that used Tutte's model to emulate the German Lorenz machine. It was programmed via switches and plugs with the wheel settings determined by the Bletchley cryptographers, read in the encrypted message from paper tape and typed out the decrypt as German plaintext).[39]
Heath Robinson
Newman, head of the Newmanry, charged with research into machinery to aid in cryptanalysis, advocated building machines to automate Tutte's method. Newman suggested using high-speed electronic counters to cope with the huge amount of counting of binary coincidences that the method demanded. This was inspired by Newman’s knowledge of C.E. Wynn-Williams’ prewar work at Cambridge on the electronic counting of α-particle emissions. Alan Turing, in his role as a scientific policy advisor at Bletchley Park, persuaded the authorities that the machine envisaged by Newman should be built and in December 1942, Newman was given the job of developing the requisite machinery.[40] The machine was partly electromechanical, partly electronic and dubbed “Heath Robinson,” after a British cartoonist of the period famed for his drawings of implausibly complex and fantastical machines to carry out everyday chores. The first Heath Robinson was installed at Bletchley Park in June 1943. The machine proved to be slow and unreliable, but sufficiently useful that Newman was motivated to place an order for more Robinsons with the Post Office research station.
Heath Robinson machines worked by reading two paper tapes in parallel, one containing a copy of the message of interest and the other, the χ component of the key. By making the key tape one character longer than the message tape, each of the 1,271 starting positions of the χ1 χ2 sequence was tried against the message. A count was amassed for each start position and, if it exceeded a pre-defined set total was printed out. The highest count was the most likely one to be the one with the correct values of χ1 and χ2. With these values, settings of the other χ wheels could be tried to break all five χ wheel starting positions for this message. This then allowed the effect of the χ component of the key to be removed, and the resulting modified message attacked by manual methods.[1]
The Heath Robinson had three limitations. First, the speed of the Heath Robinson was limited by the electro-mechanical devices themselves, with typical switching speeds of 5-20ms. Second, the Heath Robinson required a copy of the message paper tape to be driven side-by-side with a second tape containing the χ component of the key. These tapes had to be driven at a carefully controlled speed to remain synchronized with one another and to match the operating speed of the electro-mechanical parts. This proved difficult to do in practice and the Heath Robinson was notorious for breaking the tapes, requiring jobs to be restarted. Heath Robinson could at best operate the paper tapes at 2,000 characters per second. Thirdly, during the design phase of Heath Robinson there were difficulties with its logic unit – the so-called “combining unit.” The job had been given to F.O. Morrell’s telegraph section at Dollis Hill, and they proposed to implement XOR by means of a frequency modulator of a type used for voice-frequency telegraph signals. Because this device was analogue, signal noise would accumulate, and wrong answers often resulted.[5]
At Turing’s suggestion, Newman approached Tommy Flowers for help. (Turing and Flowers had worked together previously in connection with a relay-based machine for use against Enigma – this was not the famous “Bombe” but a machine for automatically decrypting Enigma messages once the settings were known). Flowers was introduced to Tunny and Heath Robinson, and his switching group improved the design of the combining unit and manufactured it.[4]
Flowers did not think much of the Robinson, however. The basic design had been settled before he was called in, and he was sceptical as to whether it would work.
Colossus: Flowers' Master Stroke
Having contributed to Heath Robinson, Flowers then made two crucial innovative steps leading to Colossus. First, he proposed to move to a fully electronic system capable of switching times measured in microseconds, i.e., three orders of magnitude faster. Second, he proposed that the keystream tape be replaced by a ring of electronic thyratron valves (vacuum tubes) operating at electronic speeds and therefore capable of being electronically synchronized with the message paper tape significantly reducing the problems with tape breakages. In addition, Flowers made the control facilities of Colossus more flexible than necessary for the cryptographer’s initial stated requirement for a machine to support wheel-setting, making it possible for Colossus to also be used in the task of wheel-breaking, by reprogramming the controls and connecting an auxiliary “Rectangling Gadget,” that produced the tables needed for rectangling, Tutte’s method for wheel breaking.[5]
As delivered, the first Colossus could only process one data bitstream at the time. The subsequent machines were to an improved, faster design that enabled up to five bitstreams to be processed in parallel, and the original machine was upgraded to match.
The main functional units of the Colossus machines were as follows:[5]
- A tape transport with an 8-photocell reading mechanism. Data input to Colossus was by reading a paper tape transcription of the enciphered intercepted message. This was arranged in a continuous loop so that it could be read and re-read multiple times – there being no internal storage for the data. The design overcame the problem of synchronising the electronics with the speed of the message tape by generating a clock signal from reading its sprocket holes. The speed of operation was thus only limited by the mechanics of reading the tape. During development, the tape reader was tested up to 9,700 characters per second (53 mph) before the tape disintegrated. 5,000 characters/second (40 ft/s (12.2 m/s; 27.3 mph) was settled on as the speed for regular use.
- A set of five parallel processing units that performed Boolean operations. (Note: the first Colossus initially had just one processing unit.)
- A six-character FIFO shift register, which was used both for computing the delta function (ΔZ) and for testing five different possible starting points of Tunny’s wheels in the five processing units.
- Twelve thyratron ring stores that simulated the Lorenz machine generating a bit-stream for each wheel,
- Panels of switches for specifying the program and the “set total.”
- A “span counter” that could suspend counting for part of the tape.
- A master control that handled clocking, start and stop signals, counter readout and printing.
- Five electronic counters.
- An electric typewriter.
Building Colossus
At the Post Office Research Station before the war, Flowers had explored the feasibility of using thermionic valves (vacuum tubes) for automated large-scale telephone switching.[4] His work in this area was, it appears, the earliest large-scale use of valves as devices for the purpose of automatic control. At this time, the common wisdom was that valves could never be used satisfactorily in large numbers, for they were unreliable, and in a large installation too many would fail in too short a time. However, this opinion was based on experience with radio receivers and the like, which were switched on and off frequently, subjecting valves to damaging thermal and electric shocks. What Flowers discovered was that, so long as valves were left on, they could operate reliably for very long periods. As he remarked, at the outbreak of war with Germany, he was possibly the only person in Britain who realised that valves could be used on a large scale for high-speed digital computing.[5]
In February 1943 Flowers had presented Newman with the possibility of a fully electronic machine able to generate the χ-stream (and ψ- and μ-streams) internally to supplant Heath Robinson. Many at Bletchley thought was that a machine containing the number of valves that Flowers was proposing could not work reliably, but Newman could see the potential in Flowers’ ambitious proposal.
Writing to Travis, the head of GC&CS in 1943, Newman gave priority to the two-tape Heath Robinson machine, leaving Flowers to press on with his alternative proposal.[34] Working independently at Dollis Hill, Flowers began building the fully electronic machine that he could see was necessary. Flowers says he embarked on Colossus “in the face of scepticism” from [some at] Bletchley Park. He was fortunate that his work was supported by Newman and by the management at Dollis Hill.[5]
When the first Colossus was delivered to Bletchley Park in January 1944 Newman was stunned. In Flower’s own words: “I don’t think they (Newman et al.) really understood what I was saying in detail – I am sure they didn’t — because when the first machine was constructed and working, they obviously were taken aback. They just couldn’t believe it! ... I don’t think they understood very clearly what I was proposing until they actually had the machine.”[41]
Learning of the capability of this first machine, in April 1944 the War Cabinet demanded 12 more machines. Flowers informed them they were dreaming and could only promise one more by 1st June 1944. This was built to the enhanced parallel design that gave a five-fold improvement in performance over the prototype. A further eight were built before the end of the war, at which point an eleventh machine was on the point of being delivered and a twelfth was in manufacture.[5]
Flowers was assisted in this production effort by his colleague Coombs. Coombs remembered Flowers, having produced a rough draft of his improved design for the Colossus machines, tearing it into pieces that he handed out to his colleagues for them to do the detailed design and get their team to manufacture it.[2]
The enhanced machines were in place by V-E Day (8th May 1945). Seven were used for wheel setting and three for wheel breaking. Colossus machines 2, 4, 6, 7 and 9 had an added rectangling gadget.[1]
What features set this work apart from similar achievements?
Colossus – The Best Kept Secret in Computing History
The existence of the Colossus machines was kept secret until the mid-1970s and therefore Colossus was omitted from early accounts of the history of electronic computing and not given the same credit as given to subsequent developments for the origin of the modern computer.
There are two IEEE Milestone Awards relating to early electronic computers that bracket Colossus. As explained in Section 3.4, Colossus and the Modern Computer, the first is for the Atanasoff-Berry Computer of 1939 which predated Colossus but was of a much smaller scale and never put to practical use; the second is for the ENIAC computer of 1946 which post-dates Colossus.
Standing between these two Milestones, Colossus warrants recognition as the first successful large-scale application of digital electronics to a computational task and that Colossus anticipated many subsequent electronic computer developments.
The reliability of Colossus was remarkable for its time: comparable systems such as ENIAC spent over a year in commissioning between being completed to being ready for everyday use and only one machine was ever constructed. Colossus was delivered to Bletchley Park in January 1944 and in continuous use from February 1944 onwards. By March 1944 the first machine was working reliably and efficiently enough for the British War Cabinet to demand that it be rapidly followed by a further twelve, of which nine were built and put into operation within 18 months. No other equally complex electronic device of the period was put into production and deployment at this scale.
In part this engineering success can be attributed to the fact that it was designed by telephone engineers who came from a culture of building and maintaining a highly reliable and large-scale system - the national telephone network.
Why was the achievement successful and impactful?
The Impact of Colossus
The use of Colossus significantly improved the ability of Bletchley Park to break the Lorenz cipher compared to prior manual methods and electromechanical machines and made a significant contribution to victory in Europe during World War II, due to the strategic nature of the intelligence gained.
For its time, Colossus was an electronic tour-de-force. Colossus was significantly larger than any other contemporary digital electronic device and the machines were run continuously 24 hours a day, seven days a week demonstrating that large-scale electronic systems could be reliable and put to continuous practical use. Being entirely electronic, Colossus delivered a step function improvement in codebreaking capability over previous electromechanical machines and hand methods. As stated in the General Report, Colossus doubled the output of decrypted Tunny messages by Bletchley Park.
Several of those who used Colossus went on to make significant contributions to post-World War II electronic computing, even though wartime secrecy forbad them from telling the story of Colossus directly.
Supporting texts and citations to establish the dates, location, and importance of the achievement: Minimum of five (5), but as many as needed to support the milestone, such as patents, contemporary newspaper articles, journal articles, or chapters in scholarly books. 'Scholarly' is defined as peer-reviewed, with references, and published. You must supply the texts or excerpts themselves, not just the references. At least one of the references must be from a scholarly book or journal article. All supporting materials must be in English, or accompanied by an English translation.
Justification for Citation
Six Colossus codebreaking computers operated in this building in 1944-1945.
The General Report contains a floor plan of Block-H showing six Colossus machines located there in 1944-1945:
Designed by Thomas H. Flowers of the British Post Office,
The General Report names Flowers of the British Post Office research station as the originator and designer of Colossus. Accounts by Flowers himself[5][35] and by others[2][29][30] further confirm his role as the originator, principal designer and project leader.
they enabled deciphering of encrypted radio messages transmitted between German commands across occupied Europe, North Africa, and the Soviet Union.
The General Report explains the nature of the radio network linking the German commands across occupied Europe, North Africa, and the Soviet Union, the Lorenz machines used by the Germans transmit and receive messages, and the techniques used at Bletchley Park to decipher those messages. The Report explicitly states that the advent of Colossus in 1944 was a breakthrough in deciphering messages intercepted on this network, more than doubling the output of deciphered Tunny messages.
The resulting military intelligence saved countless lives and was critical in shortening World War II.
The strategic importance of the radio messages deciphered by Bletchley Park during World War II using Colossus is explained in The General Report. Kenyon writing about the 1944 Normandy landings[6] explains how deciphered messages from Tunny convinced the allies that the Germans had fallen for the allies’ deception plans and consequently concentrated their forces in the Pas de Calais region making it safe to proceed with the D-Day landings on June 6th.
The overall contribution of the Bletchley Park codebreakers is acknowledged in a separate IEEE Milestone Award, dedicated on 1st April 2003, “On this site during the 1939-45 World War, 12,000 men and women broke the German Lorenz and Enigma ciphers, as well as Japanese and Italian codes and ciphers. They used innovative mathematical analysis and were assisted by two computing machines developed here by teams led by Alan Turing: the electro-mechanical Bombe developed with Gordon Welchman, and the electronic Colossus designed by Tommy Flowers. These achievements greatly shortened the war, thereby saving countless lives.” (IEEE Milestone https://ethw.org/Milestones:Code-breaking_at_Bletchley_Park_during_World_War_II,_1939-1945)
As the first successful large-scale computing application of digital electronics, Colossus anticipated subsequent computer developments.
Flowers in his description of Colossus[5] explains why he resorted to electronics as the means to speed up the process of deciphering Tunny messages, exploiting his unique knowledge of using electronics at scale and with high reliability in his pre-war work on automated telephone switching.
The first Colossus machine contained approximately 1,600-1,800 thermionic valves (vacuum tubes), far larger than any previous electronic computing system and the second and subsequent Colossus machines expanded to contain around 2,400 valves.
There are two IEEE Milestone Awards for early achievements in electronic computing, one for the Atanasoff-Berry Computer of 1937 and one for the ENIAC computer of 1945, The award for the Atanasoff-Berry computer states it “embodied concepts that would be central to the future development of computers,” but this machine, which predates Colossus, had only around 300 valves and never entered productive use. Colossus by contrast was used day and night by Bletchley Park and a total of ten machines were rapidly constructed between late 1943 and the end of World War 2 in May 1945. The award for the ENIAC computer states that ENIAC “established the practicality of large scale, electronic digital computers,” but as it only first entered practical use in 1946, ENIAC post-dates Colossus by two years.
The technical description by Flowers[5][7] and deeper analysis by later authors[18][19][35] describe how Colossus embodies many of the ideas embodied in the subsequent electronic digital computer including parallel processing, Boolean operations, counting and thresholding, fast paper tape input and typewriter output.
References
- ↑ 1.00 1.01 1.02 1.03 1.04 1.05 1.06 1.07 1.08 1.09 1.10 1.11 1.12 1.13 1.14 1.15 1.16 1.17 1.18 1.19 1.20 1.21 Good, J., Michie, D., Timms, G., 1945, General Report on Tunny: With Emphasis on Statistical Methods, UK Public Record Office HW 25/4 and HW 25/5.
- ↑ 2.0 2.1 2.2 2.3 2.4 2.5 Randell B., 1980, “The COLOSSUS,” in Metropolis, N., Howlett, J., Rota, G-C., ed. A History of Computing in the Twentieth Century. New York, USA: Academic Press, pp.47-92.
- ↑ Copeland, B.J., 2006, “Introduction”, in Copeland, B.J., et al., 2006, Colossus: The Secrets of Bletchley Park's Codebreaking Computers, Oxford: Oxford University Press, p.1.
- ↑ 4.0 4.1 4.2 Copeland, B.J., 2006, “Machine Against Machine”, in Copeland, B.J., et al., 2006, Colossus: The Secrets of Bletchley Park's Codebreaking Computers, Oxford: Oxford University Press, pp.64-77.
- ↑ 5.00 5.01 5.02 5.03 5.04 5.05 5.06 5.07 5.08 5.09 5.10 5.11 5.12 5.13 5.14 5.15 5.16 5.17 5.18 5.19 Flowers, T.H., 1983, “The Design of Colossus,” Annals of the History of Computing, 5 (3): 239–252, DOI:10.1109/MAHC.1983.10079, S2CID 39816473.
- ↑ 6.0 6.1 Kenyon, D., 2019, Bletchley Park and D-Day: The Untold Story of How the Battle for Normandy Was Won. New Haven and London: Yale University Press. ISBN 978-0-300-24357-4.
- ↑ 7.0 7.1 7.2 7.3 Flowers, T.H., 2006, “D-Day at Bletchley Park”, in Copeland, B.J., et al., 2006, Colossus: The Secrets of Bletchley Park's Codebreaking Computers, Oxford: Oxford University Press, pp.78-83.
- ↑ Goldstine, H., 1972, The Computer from Pascal to von Neumann, Princeton University Press, Princeton, United States.
- ↑ Zuse, K., 1962, “The Outline of a Computer Development from Mechanics to Electronics” p.176, in Randell 1982: Randell, B., (ed.) 1982, The Origins of Digital Computers: Selected Papers, 3rd edition, Berlin: Springer.
- ↑ http://www.tnmoc.org/witch
- ↑ Copeland, B.J., 2001, “Colossus and the Dawning of the Computer Age” in Erskine, R. and Smith, M., (eds), 2001, Action This Day: From Breaking of the Enigma Code to the Birth of the Modern Computer, pp.342–369, Bantam Press 2001, ISBN 978-05930491052011 (republished in Erskine, R. and Smith, M., (eds), 2011, The Bletchley Park Codebreakers, pp.305–327, Biteback Publishing Ltd, ISBN 9781849540780).
- ↑ Grier, D.A., 2005, When Computers were Human, Princeton University Press.
- ↑ Stibitz, G.R., 1940, “Computer,” in Randell 1982: Randell, B., (ed.) 1982, The Origins of Digital Computers: Selected Papers, 3rd edition, Berlin: Springer.
- ↑ http://www.AlanTuring.net/programmers_handbook
- ↑ Good, J., 1980, “Pioneering Work on Computers at Bletchley,” in Metropolis, N., Howlett, J., Rota, G-C., ed. A History of Computing in the Twentieth Century. New York, USA: Academic Press, 1980.
- ↑ 16.0 16.1 16.2 16.3 Copeland, B.J., et al., 2006, Colossus: The Secrets of Bletchley Park's Codebreaking Computers, Oxford: Oxford University Press, 462pp, ISBN 978-0-19-284055-4.
- ↑ 17.0 17.1 Sale, A., “The Colossus Rebuild,” ch. 12 of Copeland, B.J., et al., 2006, Colossus: The Secrets of Bletchley Park's Codebreaking Computers, Oxford: Oxford University Press, pp.150-156.
- ↑ 18.0 18.1 Wells, B., 2006, “The PC-User’s Guide to Colossus,” ch. 10 of Copeland, B.J., et al., 2006, Colossus: The Secrets of Bletchley Park's Codebreaking Computers, Oxford: Oxford University Press, pp.116-140.
- ↑ 19.0 19.1 19.2 Haigh, T., and Priestley, M., 2018, “Colossus and Programmability,” IEEE Annals of the History of Computing 40:4 (Oct-Dec, 2018): 5-27, DOI:10.1109/MAHC.2018.2877912.
- ↑ Price, D.A., 2021, Geniuses at War: Bletchley Park, Colossus, and the Dawn of the Digital Age, New York: Knopf, ISBN 978-0-525-52154-9, pp.206-207).
- ↑ Tutte, W.T., 1999, “The Coming of the Matroids,” in Lamb, J.D., Preece, D.A. (eds), Surveys in Combinatorics, 1999, Cambridge: Cambridge University Press, p.5.
- ↑ 22.0 22.1 22.2 Good, J., 2006, “From Hut 8 to the Newmanry,” ch. 16 of Copeland, B.J., et al., 2006, Colossus: The Secrets of Bletchley Park's Codebreaking Computers, Oxford: Oxford University Press, pp.204-222.
- ↑ Copeland, B.J., “Colossus and the Rise of the Modern Computer,” ch. 9 of of Copeland, B.J., et al., 2006, Colossus: The Secrets of Bletchley Park's Codebreaking Computers, Oxford: Oxford University Press, p.107.
- ↑ Fensom, H., 2006, “How Colossus was Built and Operated,” ch. 24 of of Copeland, B.J., et al., 2006, Colossus: The Secrets of Bletchley Park's Codebreaking Computers, Oxford: Oxford University Press, pp.297-304.
- ↑ Don Horwood, interviewed by Copeland in 2001.
- ↑ McKay, S., 2010, The Secret Life of Bletchley Park: The WWII Codebreaking Centre and the men and women who worked there, Aurum Press, London, ISBN 9781845135393.
- ↑ Randell, B., 1972, “On Alan Turing and the Origins of Digital Computers,” Machine Intelligence, 7, Edinburgh University Press, pp.3-20.
- ↑ Randell B., 1976, The COLOSSUS, Newcastle upon Tyne: Computing Laboratory, University of Newcastle upon Tyne, 90, Computing Laboratory Technical Report Series.
- ↑ 29.0 29.1 Coombs, A.W.M., 1983, ”The Making of Colossus,” IEEE Annals of the History of Computing, 5 (3): 253–259, DOI:10.1109/MAHC.1983.10085, S2CID 597530.
- ↑ 30.0 30.1 Chandler, W. W., 1983, ”The Installation and Maintenance of Colossus,” IEEE Annals of the History of Computing, 5 (3): 260–262, DOI:10.1109/MAHC.1983.10083, S2CID 15674470.
- ↑ Horwood, D.C., 1973, A technical description of COLOSSUS I, The National Archives, HW 25/24.
- ↑ Reeds, J.A., Diffie, W. and Field, J.V., 2015, Breaking Teleprinter Ciphers at Bletchley Park: An edition of I.J. Good, D. Michie, G. Timms – General Report on Tunny with Emphasis on Statistical Methods (1945). Wiley-IEEE Press, 792pp. ISBN 978-0-470-46589-9.
- ↑ Wells, B., 2010, “Unwinding Performance and Power on Colossus, an Unconventional Computer,” Natural Computing, vol. 10, pp.1383-1405.
- ↑ 34.0 34.1 Newman M., 1943, Letter to E. Travis, “Report on Progress,” 1st March 1943. Published 2024, by GCHQ in an online news article ”GCHQ celebrates 80 years of Colossus,” (https://www.gchq.gov.uk/news/colossus-80).
- ↑ 35.0 35.1 35.2 Flowers, T.H., 2006, “Colossus”, in Copeland, B.J., et al., 2006, Colossus: The Secrets of Bletchley Park's Codebreaking Computers, Oxford: Oxford University Press, pp.91-100.
- ↑ Bauer, F., 2006, “The Tiltman Break,” in Copeland, B.J., et al., 2006, Colossus: The Secrets of Bletchley Park's Codebreaking Computers, Oxford: Oxford University Press, pp.370-377.
- ↑ Tutte, W.T., 2006, “My Work at Bletchley Park”, in Copeland, B.J., et al., 2006, Colossus: The Secrets of Bletchley Park's Codebreaking Computers, Oxford: Oxford University Press, pp.352-369.
- ↑ Roberts, J., 2006, “Major Tester’s Section”, in Copeland, B.J., et al., 2006, Colossus: The Secrets of Bletchley Park's Codebreaking Computers, Oxford: Oxford University Press, pp.249-259.
- ↑ Hayward, G., 2006, “The British Tunny Machine”, in Copeland, B.J., et al., 2006, Colossus: The Secrets of Bletchley Park's Codebreaking Computers, Oxford: Oxford University Press, pp.291-296.
- ↑ Copeland, B.J., 2006, “Machine Against Machine”, in Copeland, B.J., et al., 2006, Colossus: The Secrets of Bletchley Park's Codebreaking Computers, Oxford: Oxford University Press, pp.64-77.
- ↑ Flowers, T.H., 1976, Flowers in interview with Christopher Evans, “The Pioneers of Computing: An Oral History of Computing,” London Science Museum.
Annotated Bibliography
The primary evidence in support of the Colossus story is contained within the release by the UK Government of the secret 1945 document written by the Bletchley Park codebreakers themselves:
1) Good, J., Michie, D., Timms, G., 1945, General Report on Tunny: With Emphasis on Statistical Methods, UK Public Record Office HW 25/4 and HW 25/5.
An annotated version of the report is available with commentary that clarifies the often difficult language of the original and fitting it into a variety of contexts arising out of several separate but intersecting story lines, some only implicit in the original, including an exploration of the likely roots of the ideas entering into the Tunny cryptanalysis, examples of original worksheets, and printouts of the Tunny-breaking process in action along with additional commentary, biographies, glossaries, essays, and bibliographies.
2) Reeds, J.A., Diffie, W. and Field, J.V., 2015, Breaking Teleprinter Ciphers at Bletchley Park: An edition of I.J. Good, D. Michie, G. Timms – General Report on Tunny with Emphasis on Statistical Methods (1945), Wiley-IEEE Press, 792pp, ISBN 978-0-470-46589-9.
In 2024, in celebration of the 80th anniversary year of Colossus, GCHQ released a copy of a letter from M. Newman to E. Travis (head of GCHQ) describes Flowers’ proposal to build an electronic machine.
3) Newman M.,1943, Letter to E. Travis, “Report on Progress,” 1st March 1943. Media:Image_Travis_letter_1943.png
Randell first documented his early discovery of information about Colossus in a 1972 paper:
4) Randell, B., 1972, “On Alan Turing and the Origins of Digital Computers,” Machine Intelligence, 7, Edinburgh University Press, pp.3-20.
After interviewing members of the Post Office Research Laboratory team, he issued a technical report, the basis of the paper presented in 1976 at a Los Alamos conference on the history of computing.
5) Randell B., 1976, The COLOSSUS. Newcastle upon Tyne: Computing Laboratory, University of Newcastle upon Tyne, 1976. Computing Laboratory Technical Report Series 90.
An expanded version of the technical report was subsequently published as a book chapter.
6) Randell B., 1980, “The COLOSSUS,” in Metropolis, N., Howlett, J., Rota, G.-C, ed., A History of Computing in the Twentieth Century, New York, USA: Academic Press, pp.47-92.
From that time an increasing number of articles and books have been written about Colossus.
The September 1983 issue of the IEEE Annals of the History of Computing was devoted to Colossus and includes accounts by Flowers and his colleagues of the development of Colossus.
7) Flowers, T.H., 1983, “The Design of Colossus,” Annals of the History of Computing, 5 (3): 239–252, DOI:10.1109/MAHC.1983.10079, S2CID 39816473.
8) Coombs, A.W.M. 1983, “The Making of Colossus,” IEEE Annals of the History of Computing, 5 (3): 253–259, DOI:10.1109/MAHC.1983.10085, S2CID 597530.
9) Chandler, W.W. 1983, “The Installation and Maintenance of Colossus,” IEEE Annals of the History of Computing, 5 (3): 260–262, DOI:10.1109/MAHC.1983.10083, S2CID 15674470.
In 2003, GCHQ declassified and released a retrospective technical description of the first Colossus to the UK National Archives.
10) Horwood, D.C. 1973, A technical description of COLOSSUS I, The National Archives, HW 25/24.
In 2004, based on interviews and on documents only recently declassified at the time, Copeland wrote an Annals of the History of Computing article clarifying the roles played by Thomas Flowers, Alan Turing, William Tutte, and Max Newman in the events leading to the installation of the first Colossus at Bletchley Park, Britain’s wartime codebreaking establishment:
11) Copeland, B.J., 2004, “Colossus: its origins and originators,” IEEE Annals of the History of Computing, 26 (4): 38–45, December 2004, DOI:10.1109/MAHC.2004.26, S2CID 20209254.
In 2006, Copeland edited and published in book form a significant collection of essays, personal recollections and human stories containing information that until then had been classified wartime material. The book gave important accounts of Colossus, many published for the first time.
12) Copeland, B.J., et al., 2006, Colossus: The Secrets of Bletchley Park’s Codebreaking Computers, Oxford: Oxford University Press, ISBN 978-0-19-284055-4. Paperback edition published in 2010.
A discussion about the "programmability" of Colossus in relation to modern concepts of programming appears the following paper which also gives one of the simpler descriptions of the architecture and capabilities of Colossus and way in which it was set up for different decryption tasks.
13) Haigh, T. and Priestley, M., 2018, “Colossus and Programmability,” IEEE Annals of the History of Computing 40:4 (Oct-Dec, 2018): 5-27, DOI:10.1109/MAHC.2018.2877912.
The impact of the Tunny decrypts on D-Day is told in:
14) Kenyon, D., 2019, Bletchley Park and D-Day: The Untold Story of How the Battle for Normandy Was Won, New Haven and London: Yale University Press. ISBN 978-0-300-24357-4.
A 2020 paper by Haigh and Priestley explores the context in which Colossus was developed and deployed, comparing the cultures at Dollis Hill and Bletchley Park and the successful symbiosis between them. The paper revisits many of the early stories and anecdotes of the pioneers that have been report since Randell’s first discoveries and offers alternative interpretations to many of the other sources.
15) Haigh, T., and Priestley, M., 2020, “Contextualizing Colossus: Codebreaking Technology and Institutional Capabilities,” Technology and Culture 61(3), 871-900. DOI:10.1353/tech.2020.0077.
In 2021 Price published a biographical history of Colossus and of the people who built and used it at Bletchley and their post war contributions to digital computing. It also the presents a counter argument to those made in the article by Haigh and Priestley in (13) on the programmability of Colossus, claiming that Colossus was not a computer.
16) Price, D.A., 2021, “Geniuses at War: Bletchley Park, Colossus, and the Dawn of the Digital Age," New York: Knopf. ISBN 978-0-525-52154-9.
Of interest to theoretical computer scientists, the mathematician Benjamin Wells has argued that a Universal Turing Machine can be run on a cluster of Colossus machines and further argued further that "a single late Colossus Mark 2 endowed with an appropriate tape punch and controller" can implement a universal Turing machine —specifically Alastair Hewitt's 2-state, 3-symbol machine, proposed in 2007.
17) Wells, B., 2004, “A Universal Turing Machine Can Run on a Cluster of Colossi,” Abstracts of the American Mathematical Society, 25: p.441.
18) Wells, B., 2010, “Unwinding Performance and Power on Colossus, an Unconventional Computer,” Natural Computing, vol. 10, pp. 1383-1405.
Colossus on YouTube
1) Stanford University, 2012: Turing: Pioneer of the Information Age, Jack Copeland, introduced by Steven Ericsson-Zenith.
2) Google, 2012: Colossus: Creating a Giant.
3) The National Museum of Computing, 2013: Uncovering Colossus, Professor Brian Randell.
4) Computer History Museum, 2013: From Codebreaking to Computing: Remembrances of Bletchley Park 50 Years Later.
5) Computer History Museum, 2015: Colossus Breaking the Code.
6) Computerphile, 2015: Colossus and Bletchley Park.
7) Centre for Computing History, 2020: Colossus – The Greatest Secret in Computing.
8) Peter Hart, 2021: Tommy Flowers & Colossus.
Supporting materials (supported formats: GIF, JPEG, PNG, PDF, DOC): All supporting materials must be in English, or if not in English, accompanied by an English translation. You must supply the texts or excerpts themselves, not just the references. For documents that are copyright-encumbered, or which you do not have rights to post, email the documents themselves to ieee-history@ieee.org. Please see the Milestone Program Guidelines for more information.
Photographs
Figure 1: Colossus at Bletchley Park 1944. Source: GCHQ, Crown Copyright. Media:Image_Colossus_1944.jpg
Figure 2: Block-H, Bletchley Park, 2024. Source: Ted Coles, The National Museum of Computing. Media:Image_Block-H_2024.jpg
Figure 3: Lorenz SZ42 machine. Source: The National Museum of Computing. Media:Image_LorenzSZ42.jpg
Figure 4:Tommy Flowers as a young man. Media:Image_Tommy_Flowers.jpg
Figure 5: Colossus at GCHQ in 1963. Source: GCHQ, Crown Copyright. Media:Image_Colossus_1963.jpg
Figure 6: Colossus Reconstruction. Source:The National Museum of Computing. Media:Image_Colossus_Reconstruction.jpeg
Figure 7: Colossus Commemorative Postage Stamp. Source: Royal Mail. Media:Colossus_stamp.jpeg
Please email a jpeg or PDF a letter in English, or with English translation, from the site owner(s) giving permission to place IEEE milestone plaque on the property, and a letter (or forwarded email) from the appropriate Section Chair supporting the Milestone application to ieee-history@ieee.org with the subject line "Attention: Milestone Administrator." Note that there are multiple texts of the letter depending on whether an IEEE organizational unit other than the section will be paying for the plaque(s).
Please recommend reviewers by emailing their names and email addresses to ieee-history@ieee.org. Please include the docket number and brief title of your proposal in the subject line of all emails.