Milestone-Proposal:Advanced Encryption Standard (AES)
To see comments, or add a comment to this discussion, click here.
Docket #:2023-24
This proposal has been submitted for review.
To the proposer’s knowledge, is this achievement subject to litigation? No
Is the achievement you are proposing more than 25 years old? Yes
Is the achievement you are proposing within IEEE’s designated fields as defined by IEEE Bylaw I-104.11, namely: Engineering, Computer Sciences and Information Technology, Physical Sciences, Biological and Medical Sciences, Mathematics, Technical Communications, Education, Management, and Law and Policy. Yes
Did the achievement provide a meaningful benefit for humanity? Yes
Was it of at least regional importance? Yes
Has an IEEE Organizational Unit agreed to pay for the milestone plaque(s)? Yes
Has the IEEE Section(s) in which the plaque(s) will be located agreed to arrange the dedication ceremony? Yes
Has the IEEE Section in which the milestone is located agreed to take responsibility for the plaque after it is dedicated? Yes
Has the owner of the site agreed to have it designated as an IEEE Milestone? Yes
Year or range of years in which the achievement occurred:
1995-1998
Title of the proposed milestone:
Rijndael and the Advanced Encryption Standard (AES), 1995 - 1998
Plaque citation summarizing the achievement and its significance; if personal name(s) are included, such name(s) must follow the achievement itself in the citation wording: Text absolutely limited by plaque dimensions to 70 words; 60 is preferable for aesthetic reasons.
In 1995-1998, Rijndael, an innovative and computationally efficient series of secure block ciphers for encrypting data and providing provable security against attacks, was created by Belgian cryptographers Joan Daemen and Vincent Rijmen. In 2000, their design won an international competition sponsored by NIST (National Institute of Standards and Technology, USA). Rijndael became the basis of AES in 2001, leading to its worldwide use for data security, encryption, and authentication.
200-250 word abstract describing the significance of the technical achievement being proposed, the person(s) involved, historical context, humanitarian and social impact, as well as any possible controversies the advocate might need to review.
Encryption is essential in protecting privacy of citizens in communication via the internet and many other communication channels. Additionally, cryptography is used to secure the remote control and management of devices and infrastructure critical in modern society: the electricity grid, the Internet itself, software updates in computers and appliances, control systems in cars, buses and trains, etc. Rijndael, after having been selected AES by NIST has played a central role worldwide to protect information from unauthorized access. Virtually all present-day systems that need cryptography use AES/Rijndael.
IEEE technical societies and technical councils within whose fields of interest the Milestone proposal resides.
Information Theory Society, Computer Society, Circuits and Systems Society
In what IEEE section(s) does it reside?
Benelux section
IEEE Organizational Unit(s) which have agreed to sponsor the Milestone:
IEEE Organizational Unit(s) paying for milestone plaque(s):
Unit: Benelux Section
Senior Officer Name: Alex Yarovoy
IEEE Organizational Unit(s) arranging the dedication ceremony:
Unit: IEEE Benelux Section Life Member Affinity Group
Senior Officer Name: Wim van Etten
IEEE section(s) monitoring the plaque(s):
IEEE Section: Benelux Section
IEEE Section Chair name: Alex Yarovoy
Milestone proposer(s):
Proposer name: Wim van Etten
Proposer email: Proposer's email masked to public
Proposer name: Luc Claesen
Proposer email: Proposer's email masked to public
Please note: your email address and contact information will be masked on the website for privacy reasons. Only IEEE History Center Staff will be able to view the email address.
Street address(es) and GPS coordinates in decimal form of the intended milestone plaque site(s):
Kasteelpark Arenberg 1, B-3001 Heverlee, Belgium. GPS coordinates: 50.86349255647128, 4.683399838914593
Describe briefly the intended site(s) of the milestone plaque(s). The intended site(s) must have a direct connection with the achievement (e.g. where developed, invented, tested, demonstrated, installed, or operated, etc.). A museum where a device or example of the technology is displayed, or the university where the inventor studied, are not, in themselves, sufficient connection for a milestone plaque.
Please give the details of the mounting, i.e. on the outside of the building, in the ground floor entrance hall, on a plinth on the grounds, etc. If visitors to the plaque site will need to go through security, or make an appointment, please give the contact information visitors will need.
The proposed location of the plaque is on a dedicated wall of the famous Castle of Arenberg in Heverlee, which presently houses the offices of the Faculty of Applied Sciences of the University of Leuven (KU Leuven, Belgium).
The creative activities that led to the invention took place in the immediate institutional neighborhood of the Castle (at the department of Electrical Engineering) as well as in the homes of the inventors in the general neighborhood. The Castle is an impressive landmark, centrally located in the Heverlee Engineering Campus of KU Leuven and a popular symbol of the political and scientific standing of the Low Countries since the Middle Ages. It attracts not only visiting tourists but scientists from over the world attending Ph.D. defenses and international conferences on its premises, where also the two inventors defended their Ph.D. theses.
Are the original buildings extant?
Yes
Details of the plaque mounting:
The plaque will be mounted on an outside wall of the courtyard of the Arenberg Castle.
How is the site protected/secured, and in what ways is it accessible to the public?
This location is freely accessible during daytime. During nighttime the area is patrolled by the university security guard.
Who is the present owner of the site(s)?
The University of Leuven (KU Leuven)
What is the historical significance of the work (its technological, scientific, or social importance)? If personal names are included in citation, include detailed support at the end of this section preceded by "Justification for Inclusion of Name(s)". (see section 6 of Milestone Guidelines)
Encryption is essential in protecting privacy of citizens in communication via the internet and many other communication channels. Additionally, cryptography is used to secure the remote control and management of devices and infrastructure critical in modern society: the electricity grid, the Internet itself, software updates in computers and appliances, control systems in cars, buses and trains etc. Rijndael, after have been selected AES by NIST has played a central role worldwide to protect information from unauthorized access.
Almost all present-day systems that need cryptography use AES/Rijndael. Examples are: modern processors from Intel, AMD, ARM, … have built-in AES instructions in their instruction set. AES is foreseen as standard in the Windows operating system, AES is used in the securing of smart cards (like payment cards), AES is the standard encryption system for Voice over IP (VoIP) communication like Skype, AES is used in WPA2 and WPA3. AES is one of the encryption algorithms in TLS (https) and IPSec, in 3G, 4G and 5G. The USA Committee on National Security Systems approved in its policy CNSSP #15 the use of AES for protection of top-secret documents. NIST claims that the AES standard resulted in an economic benefit of more than 250 billion US$, see https://www.nist.gov/news-events/news/2018/09/nists-encryption-standard-has-minimum-250-billion-economic-benefit.
Justification for Inclusion of Names in citation
The AES encryption system was developed by Joan Daemen and Vincent Rijmen as a result of research during their PhD studies at KU Leuven. They were the only two people who were involved, and together they finalized the task. In particular, they developed the underlying theory, designed the blockcipher, wrote the reference implementations, tested the security, and provided the security proofs or arguments.
As a result, these two gentlemen have gained recognition as being two of the world’s top experts on cryptography, and they have documented this in their recent biographies. Since the time of this recognition, they became university professors: dr. Daemen at University of Nijmegen (Netherlands) and dr. Rijmen at KU Leuven (Belgium).
What obstacles (technical, political, geographic) needed to be overcome?
An encryption standard has to meet formidable challenges to be effective. The US agency NIST (National Institute of Standards and Technology) initiated a five-year process during which fifteen competing designs were involved in a thorough competition and evaluation of efforts at breaking the encryption scheme in each design. In 2000, the Rijndael cipher was selected as the most suitable. When AES based on Rijndael was announced by the NIST as U.S. FIPS PUB 197 (FIPS 197) on November 26, 2001, AES became an international standard for use in data security, encryption, and authentication. On the list of participants to this competition were most of the world’s best cryptographers and companies, including Ron Rivest (the “R” of RSA), Bruce Schneier, IBM, Deutsche Telekom, Eli Biham (the inventor of differential cryptanalysis, which was the first attack to break the previous standard block cipher, the Data Encryption Standard (DES)).
In order to obtain recognition as reigning cryptography standard, another very serious obstacle that an encryption standard has to overcome, is computational efficiency on a wide variety of computing platforms, ranging from low-end embedded processors over smartcard, CPU processors, Internet servers and dedicated hardware accelerators. AES-Rijndael combines cryptographic robustness with processing efficiency in a unique and most remarkable way. It can be implemented in small applets, can easily fit in a few kbytes of RAM, but can also use vector instructions and other idiosyncrasies of advanced CPUs. It has a very efficient key setup procedure, which allows a secure Internet router to switch connections very quickly. In dedicated hardware, many trade-offs between speed and area can be made thanks to the internal symmetries of the cipher and its rich mathematical structure, e.g., the use of the multiplicative inverse in the finite field with 256 elements which can be represented and implemented in many different ways.
The most important political achievement is that this is the first encryption standard that was developed without involvement of national security agencies. The design process as well as the evaluation process were open and fully documented. This was not the case with earlier encryption standards. Note also that during the 1990’s, the USA government imposed export control on cryptographic software and hardware. The fact that the new encryption standard was designed outside the USA has contributed to the relaxation of these export controls.
What features set this work apart from similar achievements?
Rijndael has superseded DES after the latter had been shown to be too weak. Up to now Rijndael has not been broken (see documentation below.) Rijndael is the archetypical example of multi-disciplinary design requiring on the one hand deep mathematical insight and expertise on computer hardware and software architecture on the other. It is optimal in the sense that all its design elements are strictly required for security: taking away one of them would result in an insecure cipher. As a special element of the magnitude of this achievement, is the fact that it has been realized by two young researchers, dr. Joan Daemen and dr. Vincent Rijmen. These two have meanwhile obtained recognition as belonging to few world’s top experts on cryptography, as is documented by their recent biographies.
AES was innovative in cryptography as it is a radical departure of Feistel block ciphers, dominating symmetric cryptography at the time. It introduced computation on bytes, interpreted as elements of a finite field, rather than bits. It adopted a high level of symmetry and was designed according to the innovative wide trail strategy introduced by dr. Joan Daemen a few years earlier.
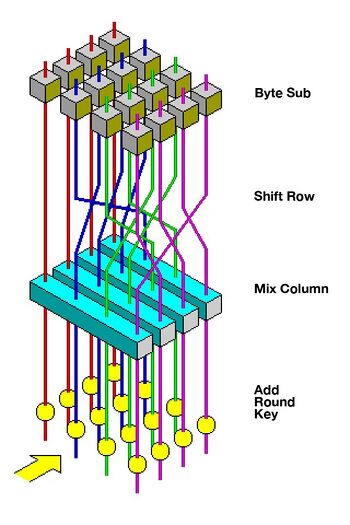
The ciphers leading to AES introduced so-called MDS mappings in symmetric cryptography. MDS mappings are derived from maximal-distance error-correcting codes. Their use allows to achieve very efficient diffusion of plaintext statistics. Fig. 3 illustrates one round of AES. Starting at the top, we see that 128 bits, represented by 4x4 bytes, are transformed by local substitutions. Subsequently the bytes are shuffled and then mixed in groups of four bytes, and finally added to 16 bytes derived from the secret key. These operations are repeated 10, 12 or 14 times to encrypt a single block of text.
The innovative design made it possible to achieve a large improvement on the state of the art with respect to provable security against the most important types of cryptanalytic attacks. NIST cited the simple structure of the design and the elegant security proofs as reasons for its selection. The AES design strategy has meanwhile been adopted by many other designers. Every textbook on Cryptography contains a section or a chapter on the AES.
Finally, the design is available royalty-free to everyone and for all uses. There are no applicable patents.
Why was the achievement successful and impactful?
The achievement is impactful because the AES and the underlying blockcipher Rijndael are widely used in IPSec, TLS, WPA2, 5G, file and disk encryption tools, smartcards, EMV, etc. Moreover, it was successful because the algorithm withstood all important types of cryptanalytic attacks. The design is available royalty-free to everyone and for all users. There are no applicable patents. For reasons given before NIST selected the design as a cryptographic standard to protect information from unauthorized access.
Supporting texts and citations to establish the dates, location, and importance of the achievement: Minimum of five (5), but as many as needed to support the milestone, such as patents, contemporary newspaper articles, journal articles, or chapters in scholarly books. 'Scholarly' is defined as peer-reviewed, with references, and published. You must supply the texts or excerpts themselves, not just the references. At least one of the references must be from a scholarly book or journal article. All supporting materials must be in English, or accompanied by an English translation.
References:
1. J. Daemen and V. Rijmen, "The Design of Rijndael – The Advanced Encryption Standard (AES)", Springer, 2002. https://doi.org/10.1007/978-3-662-04722-4. {Media:Ref-1.pdf}
2. J. Daemen and V. Rijmen, "The Design of Rijndael – The Advanced Encryption Standard (AES)", second edition, Springer, 2020. https://doi.org/10.1007/978-3-662-60769-5. {Media:Ref-2.pdf}
3. J. Daemen, "Cipher and Hash Function Design; strategies based on linear and differential cryptanalysis", PhD thesis, Katholieke Universiteit Leuven (KU Leuven), 1995. {Media:Ref-3.pdf}
4. V. Rijmen, "Cryptanalysis and Design of Iterated Block Ciphers", PhD thesis, Katholieke Universiteit Leuven (KU Leuven),1997. {Media:Ref-4.pdf}
5. J. Daemen, L.R. Knudsen and V. Rijmen, "The block cipher Square", 4th International Workshop on Fast Software Encryption, FSE'97, Haifa, Israel, January 20-22, 1997, Sprimger Proceedings, Lecture Notes in Computer Science, vol. 1267, pp. 149-165, 1997, https://doi.org/10.1007/BFb0052343. {Media:Ref-5.pdf}
6. J. Daemen and V. Rijmen, "The block cipher BKSQ", Smart Card Research and Application Conference (CARDIS) 1998, Louvain-la-Neuve, Belgium, September 14-16, 1998, Springer Proceedings, Lecture Notes in Computer Science, vol. 1820, pp. 236-245, 1998, https://doi.org/10.1007/10721064_22. {Media:Ref-6.pdf}
7. J. Daemen and V. Rijmen, "The block cipher Rijndael", Smart Card Research and Application Conference (CARDIS) 1998, Louvain-la-Neuve, Belgium, September 14-1https://doi.org/10.1007/10721064_26 6, 1998, Springer Proceedings, Lecture Notes in Computer Science, vol. 1820, pp. 277-284, 1998, https://doi.org/10.1007/10721064_26 . {Media:Ref-7.pdf}
8. J. Daemen and V. Rijmen, "The First 10 Years of Advanced Encryption", IEEE Security & Privacy, (ISSN 1540-7993), vol. 8, no. 6, pp. 72-74, 2010. {Media:Ref-8.pdf}
9. C. Bouillaguet, P. Derbez, O. Dunkelman, P. Fouque, N. Keller and V. Rijmen, "Low-Data Complexity Attacks on AES", IEEE Trans. Inf. Theory, vol. 58, no. 11, pp. 7002-7017, 2012. {Media:Ref-9.pdf}
10. B. Bilgin, B. Gierlichs, S. Nikova, V. Nikov and V. Rijmen, "Trade-Offs for Threshold Implementations Illustrated on AES", IEEE Trans. Comput. Aided Des. of Integr. Circuits and Syst., vol. 34, no. 7, pp. 1188-1200, 2015. {Media:Ref-10.pdf}
11. NIST, "Specification for the Advanced Encryption Standard (AES)", FIPS 197, 2001. {Media:Ref-11.pdf}
12. NIST, "AES Development", https://csrc.nist.gov/projects/cryptographic-standards-and-guidelines/archived-crypto-projects/aes-development. {Media:Ref-12.pdf}
13. Wikipedia, "Advanced Encryption Standard", https://en.wikipedia.org/wiki/Advanced_Encryption_Standard. {Media:Ref-13.pdf}
14. CNSS, "National Policy on the Use of the Advanced Encryption Standard (AES) to Protect National Security Systems and National Security Information", CNSS Policy No. 15, Fact Sheet No. 1, June 2003. {Media:Ref-14.pdf}
15. X. Zhang and K.K. Parhi, "High-speed VLSI architectures for the AES algorithm", IEEE Transactions on Very Large Scale Integration (VLSI) Systems, vol. 12, no. 9, pp. 957-967, 2004. {Media:Ref-15.pdf}
16. G. Bertoni, L. Breveglieri, I. Koren, P. Maistri and V. Piuri, "Error analysis and detection procedures for a hardware implementation of the advanced encryption standard", IEEE Transactions on Computers, vol. 52, no. 4, pp. 492-505, 2003. {Media:Ref-16.pdf}
17. J. Wolkerstorfer, E. Oswald and M. Lamberger, "An ASIC Implementation of the AES Sboxes", Cryptographers’ Track of the RSA Conference (CT-RSA) 2002, Springer, Lecture Notes in Computer Science, vol. 2271, pp. 67-78, https://doi.org/10.1007/3-540-45760-7_6. {Media:Ref-17.pdf}
18. D. Gullasch, E. Bangerter and S. Krenn, "Cache Games -- Bringing Access-Based Cache Attacks on AES to Practice", IEEE Symposium on Security and Privacy, pp. 490-505, 2011. {Media:Ref-18.pdf}
Supporting materials (supported formats: GIF, JPEG, PNG, PDF, DOC): All supporting materials must be in English, or if not in English, accompanied by an English translation. You must supply the texts or excerpts themselves, not just the references. For documents that are copyright-encumbered, or which you do not have rights to post, email the documents themselves to ieee-history@ieee.org. Please see the Milestone Program Guidelines for more information.
Please email a jpeg or PDF a letter in English, or with English translation, from the site owner(s) giving permission to place IEEE milestone plaque on the property, and a letter (or forwarded email) from the appropriate Section Chair supporting the Milestone application to ieee-history@ieee.org with the subject line "Attention: Milestone Administrator." Note that there are multiple texts of the letter depending on whether an IEEE organizational unit other than the section will be paying for the plaque(s).
Please recommend reviewers by emailing their names and email addresses to ieee-history@ieee.org. Please include the docket number and brief title of your proposal in the subject line of all emails.